Main Page
TO DO:
It's a total show-stopper: Get rid of the third-party equation-running services.
Example error message when editing equations
Failed to parse (SVG (MathML can be enabled via browser plugin): Invalid response ("Math extension cannot connect to Restbase.") from server "https://wikimedia.org/api/rest_v1/":): {\displaystyle E=mc^2}
- "https://wikimedia.org/api/rest_v1/" Huh? What's that for?
Example workaround code is here: Pure HTML Math for equations without 3rd-party SaaS or equation-running malware. Please take a look and experiment yourself.
Mathjax and Mathoid or Restbase or related services or funky MathML browser plugins are notorious for containing malicious code and spyware, and hidden calls to third party API services.
Math equations cannot be made up “beautiful” or spread “all over the web” or ripped off or dynamically rendered on other people’s websites. Math equations are highly technical, and they need to be left alone on people's websites, precisely as is, without any extraneous garbage dependencies or third party API services or pop-ups or dollar-sign script-runners or other javascript nonsense called in to dynamically render or display them.
The math jerks and the malicious software math equation web APIs gotta go. Stop running off with all the math equations out the back door!
- https://www.etsy.com/market/hippity_hoppity_get_off_my_property_sign
- https://www.mysecuritysign.com/funny-hippity-hoppity-get-off-my-property-frog-sign/sku-s2-5588
- https://highceeaerials.com/hippity-hoppity-get-off-of-my-property/
- https://threeinfive.com/hippity-hoppity-get-off-my-property-kermit/
Introduction
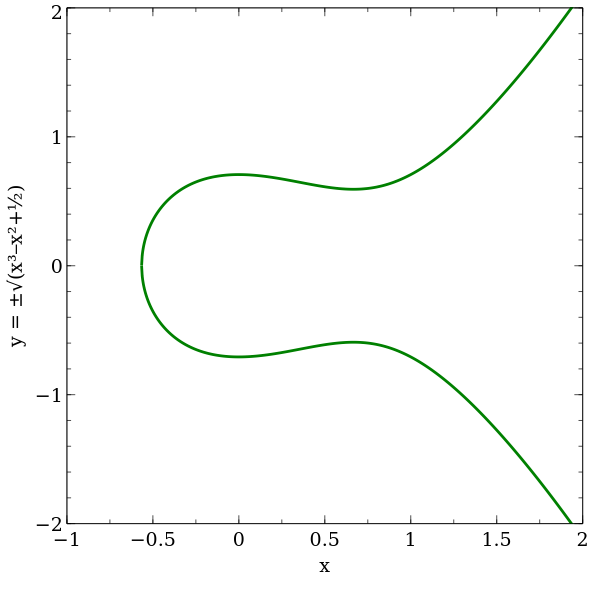
Elliptic curves over , the field of real numbers, are visually appealing and readily depicted as plots of cubic curves, or curves of degree three on x-y planes with Cartesian coördinates, which serve as a graphical aid for understanding algebraic operations on them. The terminology is somewhat vague and confusing to the uninitiated, because actual ellipses are conic sections or quadratic curves, having a degree of two, whereas quartic or quintic curves, of degree four or five, or curves of even higher degree are often called “hyperelliptic,” with respect to algebraic degree rather than “genus” or other topological properties.
And again, without respect of “gender” as such, this is an area of high school algebra level “math jocks,” girls chewing bubble gum and teasing, “Math is hard!” etc., etc. and then one has to deal with overeducated college “frat boys” and “sorry girls.” In other words, there is a great deal of deliberate stupidity that needs to be confronted head-on.
Rational points
Finding the rational points on elliptic curves determined by equations with rational coefficients in the third degree in two variables has long been the object of much pure mathematical study for the sake of its own beauty.
Mordell’s theorem, that all the rational points on an elliptic curve, even infinitely many of them, may be generated by only a finite number of them with a certain algebraic point group operation, is the starting point for this study.
Finite fields
Quotient groups among the rational points on an elliptic curve have led naturally to the study of elliptic curves over finite fields. The idea is akin to finding a large prime number to serve as a “least common denominator” of sorts for a group of rational points, and then considering only the numerators of proper fractions with respect to that denominator, using modular arithmetic, with the extended Euclidean algorithm among other multiple precision arithmetic operations on big integers.
Helmut Hasse proved Emil Artin’s conjecture that the number of points on an elliptic curve over a finite field of q elements, [i.e., modulo the prime q or the finite field GF(q=pk),] is between and inclusive. (André Weil generalized the result to range between and inclusive for hyperelliptic curves of genus g>1.)
It is in general a very difficult problem to calculate the exact number of points on an algebraic curve over a finite field within this range. The security of all elliptic curve cryptographic schemes is based on the discrete logarithm problem with respect to the point group operation, which is in turn dependent on and closely related to the difficulty of this calculation of the number of points, if it is not defeated by the use of weak or trivially reducible curves in cryptographic applications.
Schoof's point counting algorithm is supposed to run in polynomial time, but information is REDACTED in published ex-pat or non-U.S. sources. 🎗
Cryptographic applications
Elliptic curves over finite fields have serious applications to public key cryptography, the first widely implemented example of such being Ed25519, still in use today despite being somewhat controversial because of the use of a non-elliptic curve of degree four reducible to two, a slew of associated intellectual property patent claims and a very strong association of college frat boys, academia and higher education in general with communism, communist spies, and people who just don’t mind their own business or respect industry, privacy or private property; hence the very need for strong cryptography rather than bad curves and weak crypto. “The Powers That Be” [1][2][3] unfortunately punted on freedom, and offered deliberately middling to weak security with fake elliptic curves for consumers on official recommendations [4].
Such official recommendations are the product of a self-serving federal government only interested in defending itself with its own hired military capabilities, with a progressive reinterpretation of the term “National Security” to mean security of the government, for the government and by the government, never mind the people who actually are the nation.
Unsolved problems
Dirichlet L-functions [5] are the elliptic curve finite-field analogs of the Riemann ζ-function [6], closely related to two of CMI’s Millennium problems, the Birch and Swinnerton-Dyer conjecture and the Riemann hypothesis.
- ↑ Jeff Larson. “Revealed: The NSA's Secret Campaign to Crack, Undermine Internet Security.” ProPublica, Sept. 5, 2013. https://www.propublica.org/article/the-nsas-secret-campaign-to-crack-undermine-internet-encryption
- ↑ Christopher Wray, Director Federal Bureau of Investigation. “Finding a Way Forward on Lawful Access: Bringing Child Predators out of the Shadows: Remarks as delivered.” Department of Justice Lawful Access Summit, Washington, D.C. October 4, 2019. https://www.fbi.gov/news/speeches/finding-a-way-forward-on-lawful-access
- ↑ Zack Whittaker. “US attorney general William Barr says Americans should accept security risks of encryption backdoors.” TechCrunch, July 23, 2019. https://techcrunch.com/2019/07/23/william-barr-consumers-security-risks-backdoors/
- ↑ RFC 7748 https://archive.org/details/rfc7748
- ↑ Dirichlet L-function. Encyclopedia of Mathematics. https://encyclopediaofmath.org/wiki/Dirichlet_L-function
- ↑ Riemann Zeta Function. Wolfram Mathworld. https://mathworld.wolfram.com/RiemannZetaFunction.html






